Authorities in Romania have identified new malware that claims to be from police enforcing copyright and anti-porn laws.
Called
the Icepol trojan, the ransomware sends a message to victims accusing
them of software piracy or downloading illegal porn, then locks the
victim’s computer and demands payment to unlock it. It was installed on
more than 267,000 computers including in the US, Germany and Australia
and responsible for more than 148,000 scam transactions in just five
months.
Security vendor Bitdefender said Icepol originated in
Romania, the company’s own home country, and was distributed in 25
languages.
After analysing information from servers seized by police, Catalin
Cosoi, chief security strategist, Bitdefender, said the scam revealed a
larger malware distribution system. Cosoi said the criminal underworld
has developed supply-chain networks that work much in the same way as
more traditional criminal enterprises – even down to money-making
referral and syndication schemes.
Advertisement
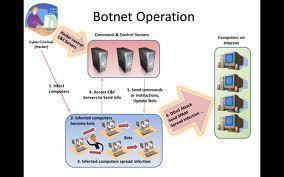
Servers were organised in a pyramid scheme where a number of
affiliates were connected to a central (command and control) server
responsible for delivering the malware. The Romanian-based unit was
communicating with a central server in The Netherlands, before it was
moved to Germany as authorities closed in.
The findings support claims made late last year by another security
firm, FireEye, about common development and logistics centers or a
‘hacking industry’. A spate of seemingly unrelated internet attacks
launched from China in 2013 was found to have used similar underlying
organised structures. The discovery prompted FireEye to warn of defence
contractor-style groups creating the tools hackers buy, trade and use.
Raymond Choo, Australian Institute of Criminology senior security analyst, agreed there was an internet crime ecosystem.
“[A big threat] to cyber-security is the asymmetrical nature of
cyberspace that can be leveraged by smaller or less technologically
advanced countries to launch [attacks] by buying or renting the services
and skills of cybercriminals,” they said.
Many experts say the concept of the ‘darknet’ – the seamy online
underbelly used to produce and swap everything from bomb recipes to
child pornography – is applicable to the hacking community, allowing
organised hacking groups to join, collaborate and disperse.
“The criminal underground is known for having an organised structure
that allows actors to specialise,” said Will Pelgrin, chief executive of
the US Centre for Internet Security. “In the last several years it’s
developed into a fee-for-service model to such an extent there are
different layers of organisation. Some malicious actors control the
money mules, others control the controllers.”
But as Nigel Phair of Canberra University’s Centre for Internet
Safety warned, the existence of such cyber arms dealer-style
fraternities doesn’t mean cybercrime will be any easier to combat.
“If cyber criminals make an exploit that works they can join
different criminal networks to profiteer from it, but I wouldn’t assume
the ‘brains trust’ behind malware is that small,” they says.
“Geographically diverse criminals who never meet may get together based
on their expertise and conduct an exploit. Once they’ve completed a
particular task and made money they go their separate ways, try
something new or try the same exploit in a different industry sector.”
But does something approaching a hacker industry make internet crime any easier to stamp out?
“Unsurprisingly, many of the high-end cyber criminals live in
jurisdictions with weak or no cybercrime laws,” said Phair, a former
Australian Federal Police officer. “And often, law enforcement doesn’t
have the capability or capacity to investigate local criminal elements.”
Still, there are points of weakness the forces of good can exploit.
Kyle Creyts, senior threat analyst at US security firm Lastline, said
internet criminals need hosts, computers and other traceable
supply-chains just like genuine businesses.
“I’d focus on the notion of administrative domain,” they said.
“When a given provider has relatively bad, slow or ineffective
response to compromises of their customers, it’s generally known and
discussed in the underground community. Some of them even go so far as
to offer what’s called ‘bulletproof’ hosting where they publicly
acknowledge or advertise that they won’t respond to abuse complaints or
law enforcement requests.”